
Creating firewall rules
- Access the Virtual Machine configuration screen.
- Click on the "Firewall rules" icon:
- The firewall configuration will appear
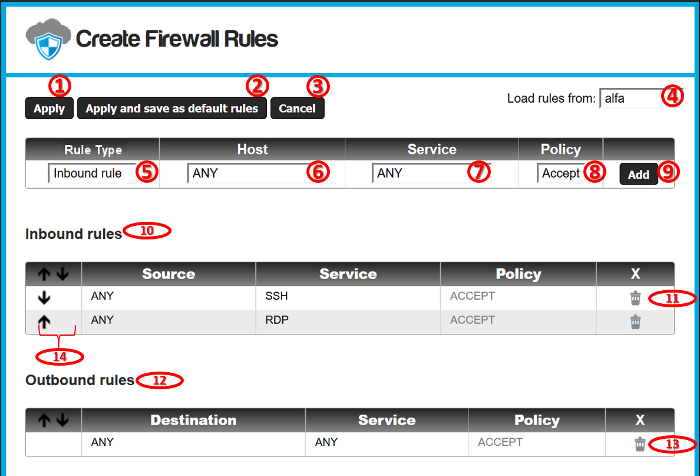
- "Apply": Apply all the rules from the current configuration.
- "Apply and save as default rules": This button applies the rules and saves them as the default rules template for new virtual machines.
- "Cancel": Discards all changes made to the configuration.
- Loads the rules from another virtual machine, in this way we can copy firewall rules sets between VMs.
- Type of the rule:
- Inbound rule: Filters connections from the Internet where the destination target is the current virtual machine.
- Outbound rule: Filters connections from the current virtual machine with destination to any public address on the internet.
- IPS Filter: Applies one of the SNORT
Intrusion Prevention System rules sets to your virtual
machine public traffic.
- Host or network to apply the current firewall rule. (See Hosts and
Networks).
- The service that will be filtered by the current rule. (See Firewall Services).
- Firewall Policy for the rule. We can accept or reject the
connections that matches the current service, with destination
or origin to the selected Hosts/Networks (depending whether it
is an inbound or outbound rule).
- Accept: Allow the communication through the selected service with the configured hosts or networks.
- Reject: Drops any connections through the current service with the configured hosts or networks. Connections fallen into the "Reject" policy will be dropped by the firewall, this means that after a connection attempt, the client won't issue a "Connection refused" message, so the connection will be ignored and probably the client should end the connection after a proper time out.
- Add button: Add the current rule to the firewall into
the inbound, outbound or IPS Filter tables.
- Inbound rules: Table to filter incoming connections to the
Virtual Machine.
- Delete button: Will delete the selected rule.
- Outbound rules: Table to filter outgoing connections from the
Virtual Machine.
- Delete button: Will delete the selected rule.
- Ascent/descent buttons to organize the firewall rules:
- The firewall reads the rules in descending order, and applies them in the same order.
- Each connection passing through the firewall is compared to each rule (inbound or outbound) until a rule that applies to that connection is found.
- The first rule in descending order that matches a specific connection will be applied, the rules under it will be ignored.
- If no rule matches a particular connection, then the connection will be denied.
- That means all services required for the proper function of
a Virtual Machine must be explicitly enabled.
IPS Filters
The Cloud-Bricks system integrates the SNORT Intrusion Prevention System so you can filter malicious traffic in your virtual network.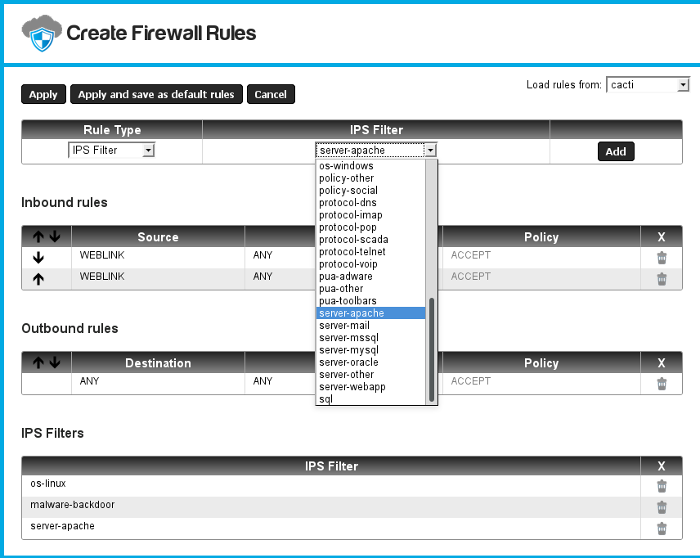
- When you select the rule type "IPS Filter" you will be able to choose between several filters to scan your network traffic in order to prevent attacks to your virtual machine.
- Each filter corresponds to one of the SNORT Intrusion Prevention System rules sets.
- Please select only the filters that actually correspond to your virtual machine operating system and software. Selecting many filters may decrease your network performance.
- The Cloud-Bricks firewall will drop any connection that tries to exploit any of the vulnerabilities described in the IPS Filters.
- You will be able to monitor the alerts raised using the SNORT I.P.S. link in the Firewall menu within the Cloud-Bricks Web Administration system.